Workflows
IBAN
Compar. App-TAN
More Information
Friendly Fraud
PSD2-Compliance
Business Partners |
Android App
iOS App
Windows App |
API Version 1
API Version 2
SDK/Library
Display-TAN/soft |
Seed Perso
Display-PIN
Online Banking Demo
IoT Applications |
nfc-tan.com
smartdisplayer.com
borchert-it-sicherheit.com
|
About
Contact
Imprint
Privacy Policy |
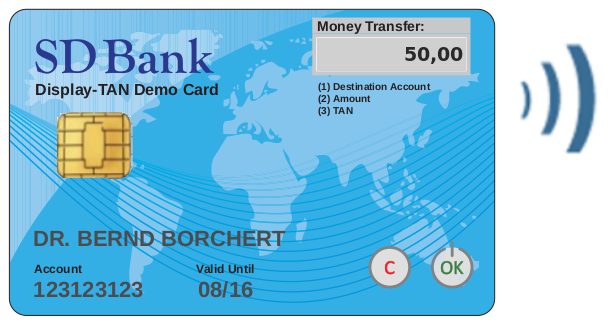 Display-TAN
Display-TAN
 Display-TAN
Display-TAN